Evil Twin - Mark VII
Learn how to set up a fake authentication web page on a fake WiFi network.
Read the comments in these two files to get a better understanding on how all of it works:
/src/evil-twin/index.php /src/evil-twin/MyPortal.phpYou can modify and expand this project to your liking. You have everything you need to get started.
You can easily customize CSS to make it look more like the company you are testing, e.g. change colors, logo, etc.
You can also use SingleFile (Chrome)(FireFox) browser extension to download a web page as a single HTML file, rename the file to index.php, and use it in the same template.
Tested on WiFi Pineapple Mark VII Basic with the firmware v2.0.0 and modules Evil Portal v1.5.1 and Cabinet v1.2.1.
Additional set up and testing was done on Windows 10 Enterprise OS (64-bit) and Kali Linux v2022.2 (64-bit).
Made for educational purposes. I hope it will help!
In this project I also want to show you how to install and use WiFi Pineapple's modules through GUI, for more console attacks check my WiFi penetration testing cheat sheet.
If you have an older device, go to WiFi Pineapple Nano (Mark VI).
Table of Contents
How to Set up a WiFi Pineapple Windows OS Kali Linux How to Run Spoof All SSIDs Kismet Remote Packet Capture Local Packet Capture Sniff WiFi Network Traffic ImagesHow to Set Up the WiFi Pineapple
In case you might need it, check frimware recovery/upgrade.
Windows OS
Follow the instructions below:
Setup Basics
Windows Setup
Kali Linux
Download and run the following script:
wget https://downloads.hak5.org/api/devices/wifipineapplemk7/tools/wp7.sh/1.0/linux -O wp7.sh && mv wp7.sh /usr/bin/wp7 && chmod +x /usr/bin/wp7 && wp7
How to Run
In WiFi Pineapple's dashboard go to Modules & Packages -> Modules -> Get Available Modules, install Evil Portal and Cabinet modules, and pin them to the sidebar.
Copy all the content from src to WiFi Pineapple's /root/portals/ directory:
scp -r evil-twin root@172.16.42.1:/root/portals/evil-twin
Go to PineAP Suite -> Open AP, and set the Open SSID to your desired (portal) name.
Go to PineAP Suite -> Filtering, and make sure both client and SSID filter lists are set to deny mode.
Connect your WiFi Pineapple to a real working WiFi network in Settings -> Networking -> Wireless Client Mode section to tunnel network traffic back and forth from the Internet.
In WiFi Pineapple's dashboard go to Evil Portal and activate the portal, then, click on both Start Web Server and Start.
In WiFi Pineapple's dashboard go to Cabinet, navigate to /root/logs/ directory and click "Edit" on evil_twin.log to view the captured credentials.
Download the log file through SSH:
scp root@172.16.42.1:/root/logs/evil_twin.log ./
Spoof All SSIDs
Hide the open access point.
In WiFi Pineapple's dashboard go to PineAP Suite -> Impersonation and add desired (portal) names to Spoofed AP Pool, then, set your settings as in picture below to spoof all the access points in your range.

Figure 1 - PineAP Settings
Find out more about PineAP Suite here.
Find out how to turn up your WiFi Pineapple's signal strength to missassociate clients to the fake WiFi network from my other project.
Use filtering so you won't go out of your testing scope.
Kismet
Search for WiFi networks within your range and fetch their MAC address, vendor name, etc.
Remote Packet Capture
On your Kali Linux, download some missing files, then, run Kismet's server:
wget https://raw.githubusercontent.com/kismetwireless/kismet/master/conf/kismet_httpd.conf -O /etc/kismet/kismet_httpd.conf
wget https://raw.githubusercontent.com/kismetwireless/kismet/master/conf/kismet_manuf.txt.gz -O /etc/kismet/kismet_manuf.txt.gz
kismet
Connect to your WiFi Pineapple (remote port forwarding) and install Kismet's remote capturing tool:
ssh root@172.16.42.1 -R 3501:localhost:3501 opkg update && opkg install kismet-capture-linux-wifi
Connect Kismet's remote capturing tool to Kismet's server:
airmon-ng start wlan0
kismet_cap_linux_wifi --tcp --connect localhost:3501 --source wlan0mon
On your Kali Linux, navigate to Kismet's dashboard (http://localhost:2501) with your preferred web browser.
Local Packet Capture
Connect to your WiFi Pineapple, then, install, download missing files, and run Kismet's server:
ssh root@172.16.42.1 opkg update && opkg install kismet wget https://raw.githubusercontent.com/kismetwireless/kismet/master/conf/kismet_httpd.conf -O /etc/kismet/kismet_httpd.conf wget https://raw.githubusercontent.com/kismetwireless/kismet/master/conf/kismet_manuf.txt.gz -O /etc/kismet/kismet_manuf.txt.gz airmon-ng start wlan0 kismet -c wlan0mon
On your Kali Linux, navigate to Kismet's dashboard (http://172.16.42.1:2501) with your preferred web browser.
Sniff WiFi Network Traffic
Once you get an access to a WiFi network, start capturing network packets.
In WiFi Pineapple's dashboard go to Modules -> Manage -> Get Available Modules, install TCPDump module, and pin it to the sidebar.
In WiFi Pineapple's dashboard go to TCPDump and start capturing packets.
You can download the PCAP file by clicking on the cloud icon.
You can also pipe tcpdump from WiFi Pineapple directly to Wireshark
ssh root@172.16.42.1 tcpdump -U -i wlan0mon -w - | wireshark -k -i -
On Windows OS you might need to specify a full path to the executable.
Images
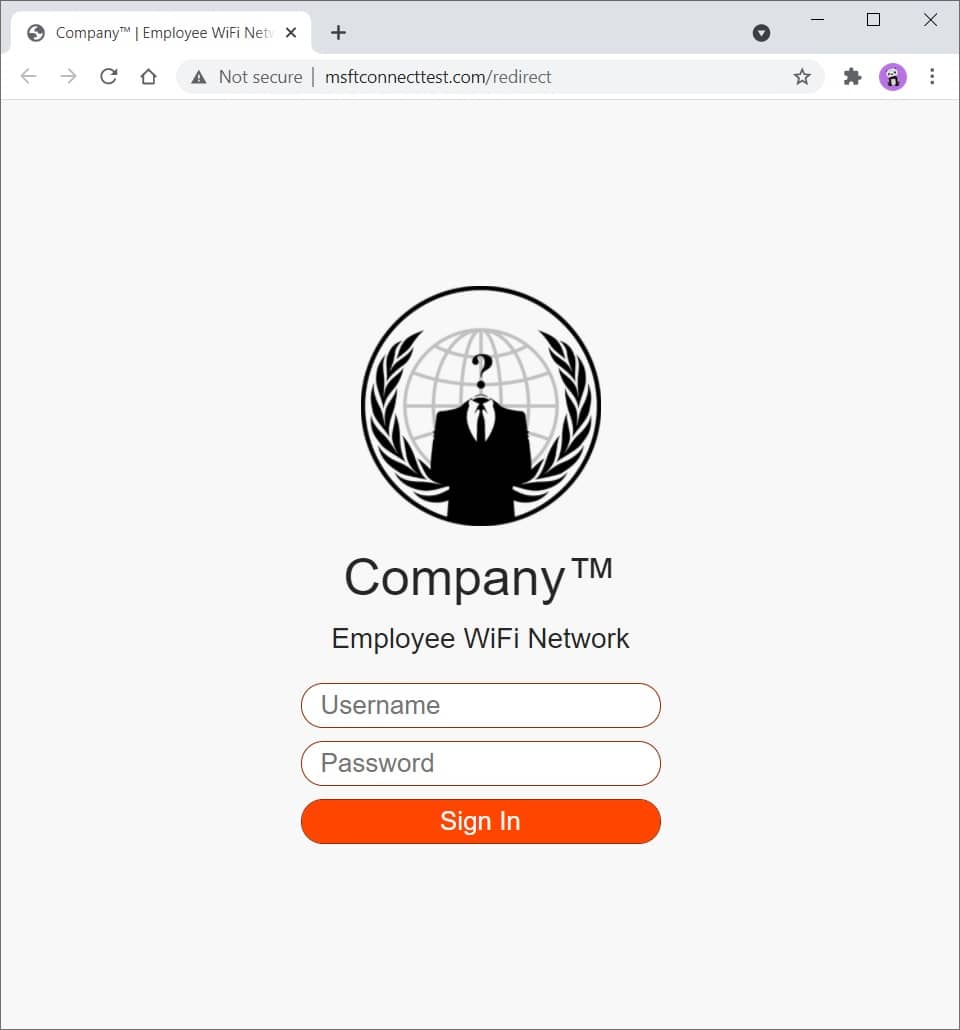
Figure 2 - Landing Page (PC)

Figure 3 - Landing Page (Mobile)
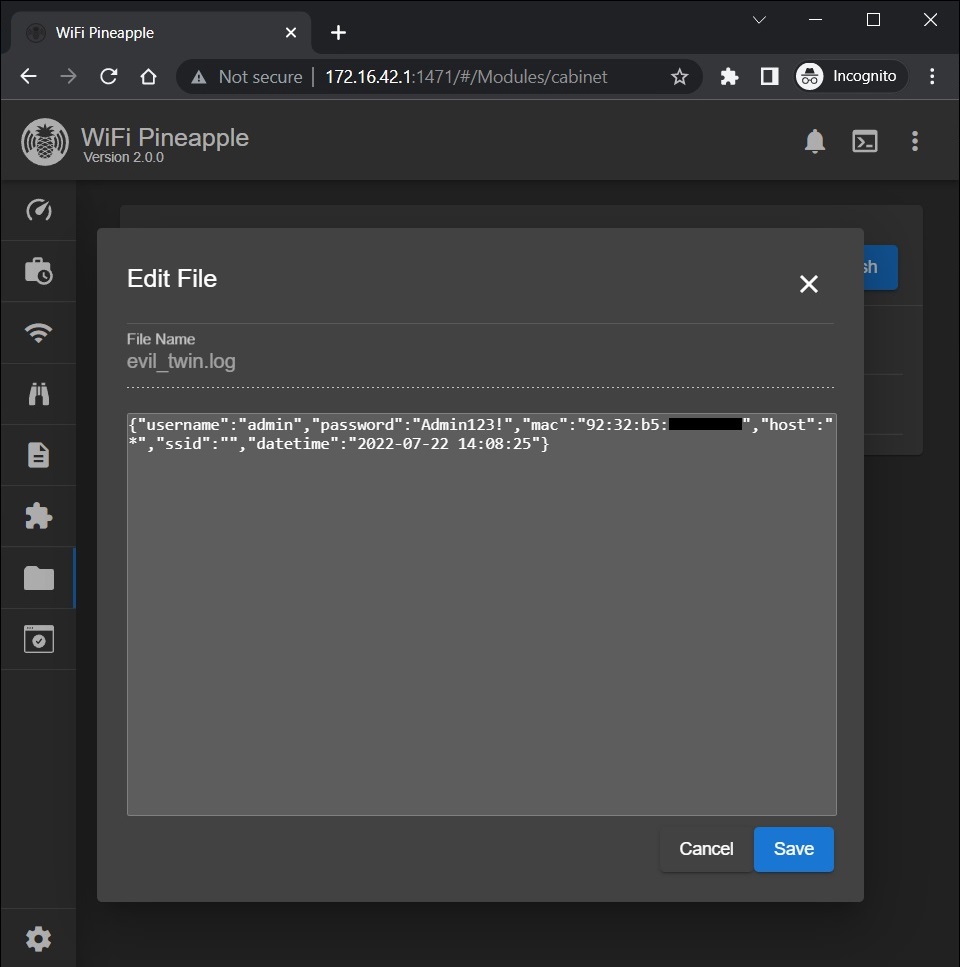
Figure 4 - Log
版权声明:
1、该文章(资料)来源于互联网公开信息,我方只是对该内容做点评,所分享的下载地址为原作者公开地址。2、网站不提供资料下载,如需下载请到原作者页面进行下载。
3、本站所有内容均由合作方或网友上传,本站不对文档的完整性、权威性及其观点立场正确性做任何保证或承诺!文档内容仅供研究参考学习用!
4、如文档内容存在违规,或者侵犯商业秘密、侵犯著作权等,请点击“违规举报”。


